Ever had an important email bounce back with a confusing “DMARC fail” message? It might seem like just a delivery glitch, but it’s actually a red flag that your email setup needs some attention.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a powerful tool that helps protect your domain from spoofing and phishing attacks. But if it’s not set up correctly, it can stop your legitimate messages from being delivered or send them straight to the spam folder.
In this guide, we’ll break down what causes a DMARC fail and show you how to fix it. With clear visuals and practical tips, you’ll get your email systems secure, compliant, and running smoothly again.
What Does a DMARC Fail Mean?
A DMARC fail means that your email didn’t pass the basic checks that prove it really came from your domain. It’s like showing up at airport security without ID. Your message might look fine on the surface, but the receiving server doesn’t trust it.
In practice, this can lead to a few things:
- Your email bounces back entirely.
- It lands in the recipient’s spam folder.
- It gets delayed or flagged as suspicious.
All of this hurts your deliverability, damages your email reputation, and can stop important messages from getting through. So, even if your message is legitimate, a failed DMARC check makes it look shady.
What Causes a DMARC Failure?
Understanding the root causes of DMARC authentication failures helps you troubleshoot issues more effectively and prevent future problems that hurt email deliverability. Most DMARC fail errors happen because something in your domain’s authentication setup doesn’t line up.
SPF and DKIM Misalignment
If your SPF record doesn’t include all the services that send mail for your domain, or your DKIM signature doesn’t match what’s in your DNS records, your messages won’t pass DMARC authentication. This often happens when new providers are added without updating DNS, or if messages get slightly altered in transit, breaking DKIM along the way.
DMARC needs either SPF or DKIM to align with the “From” domain. If neither does, even legit emails can bounce or land in spam.
DNS Record Errors
Typos, formatting issues, or missing records in your DNS can make it impossible for receiving servers to verify your DMARC policy. DNS records also need regular updates, especially as you switch services or grow your email program. If they’re not maintained, spoofing risks go up while your legit messages get blocked.
And yet, according to the FTC, most hosting providers don’t configure DMARC by default, and 27% don’t even have an option to do so.
Forwarding and Intermediate Servers
Forwarding is a common troublemaker. When emails pass through other systems—like forwarding services or mailing lists—those systems often tweak the headers or route, breaking SPF and DKIM in the process.
Since DMARC relies on verifying the original sender, these changes make it hard for the checks to confirm your identity.
Strict DMARC Policy Enforcement
Setting your DMARC policy to p=reject too early can backfire. If your SPF or DKIM setup isn’t fully aligned yet, you might start blocking legitimate emails without realizing it.
Start with a more flexible policy and move up as your configuration becomes more solid:
- p=none: This is a monitoring-only mode. Emails that fail DMARC still get delivered, but you receive DMARC aggregate reports showing which messages pass or fail authentication. It’s a safe way to detect issues without risking message loss.
- p=quarantine: Emails that fail DMARC are delivered to spam or junk folders. This adds light enforcement while still letting recipients access the messages.
- p=reject: This is full enforcement. Messages that fail DMARC checks are blocked completely and not delivered.
Each step gives you insight into how your authentication is performing, without cutting off communication too early. Use p=none as a diagnostic tool before stepping up enforcement.
Troubleshooting Steps to Fix a DMARC Fail
Getting a DMARC fail message usually means something’s off in your domain’s authentication setup. These errors affect email deliverability, trigger bounce messages, and may send your legitimate mail straight to spam folders.
To troubleshoot, follow these four steps to get your SPF, DKIM, and DMARC configuration back on track.
Step 1: Verify SPF and DKIM Authentication
DMARC relies on either SPF or DKIM (or both) to authenticate your messages. If these don’t align with your domain’s DMARC policy, messages will fail DMARC checks.
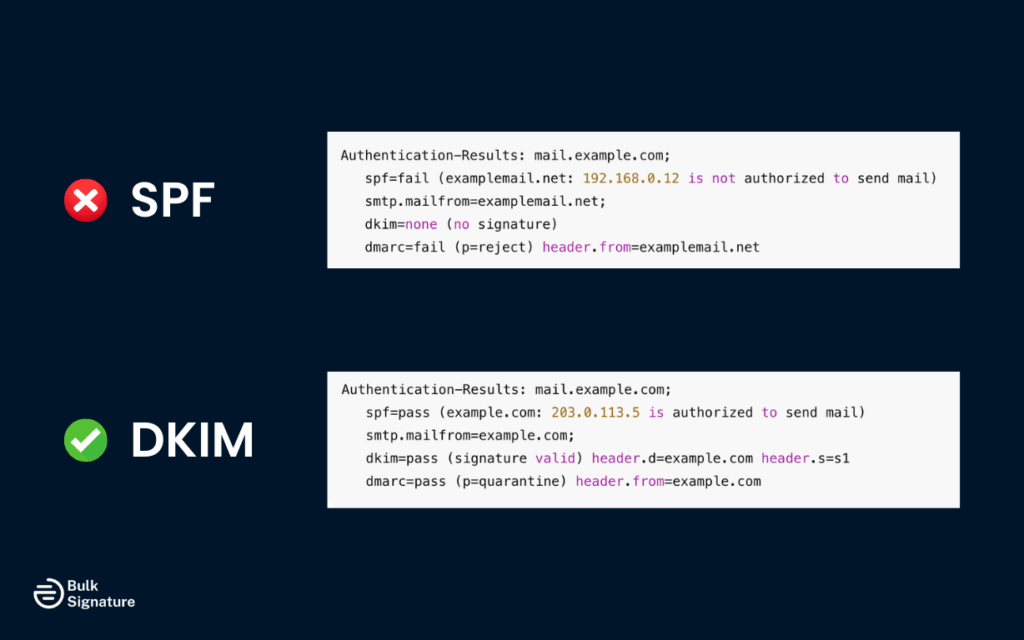
- Run an SPF check using a lookup tool to confirm your SPF record (a type of DNS TXT record) includes all the IP addresses and email services allowed to send mail for your domain.
- Check your DKIM signature to ensure outgoing messages are signed with a valid DKIM key that matches what’s published in your domain’s DNS records.
- Be aware that if a third-party email service provider modifies message content, it can break DKIM authentication and trigger DMARC failures.
Even if SPF and DKIM pass individually, your email can still fail DMARC authentication if they don’t align with the domain in the “From” header.
Step 2: Review Your DNS TXT Records
Incorrect or outdated DNS TXT record entries are a common cause of DMARC authentication failure.
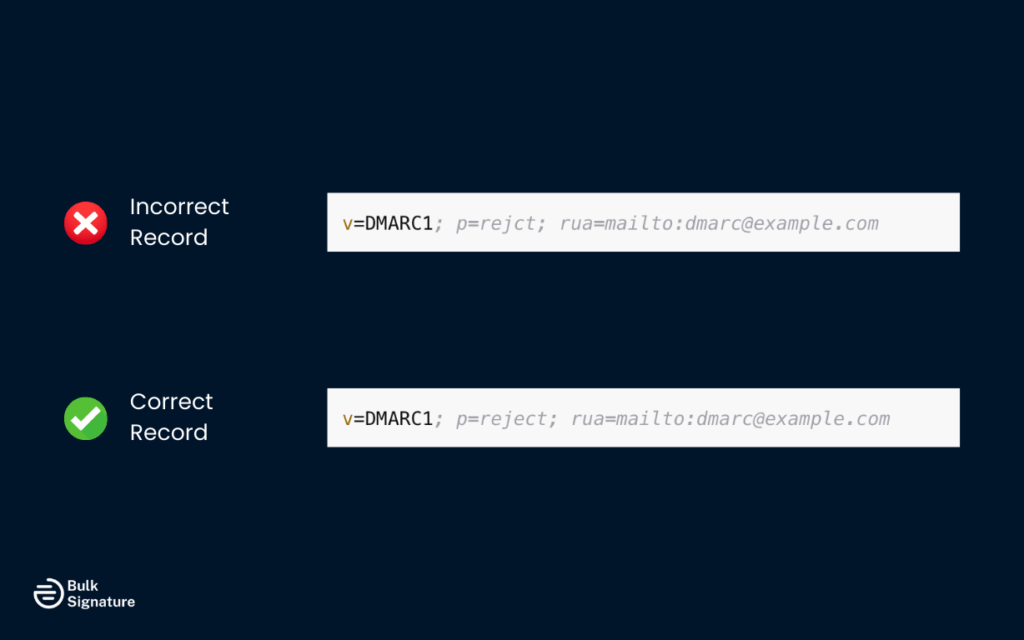
- Look for typos, missing semicolons, or invalid syntax in your DMARC record.
- Remove outdated records and make sure SPF, DKIM, and DMARC entries reflect your current mail sending practices.
- After making changes, allow time for DNS propagation and retest your records.
For example, a typo like p=rejct instead of p=reject can completely break your DMARC configuration.
Step 3: Analyze DMARC Aggregate and Failure Reports
Your DMARC reports provide essential visibility into what’s working, and what’s not.
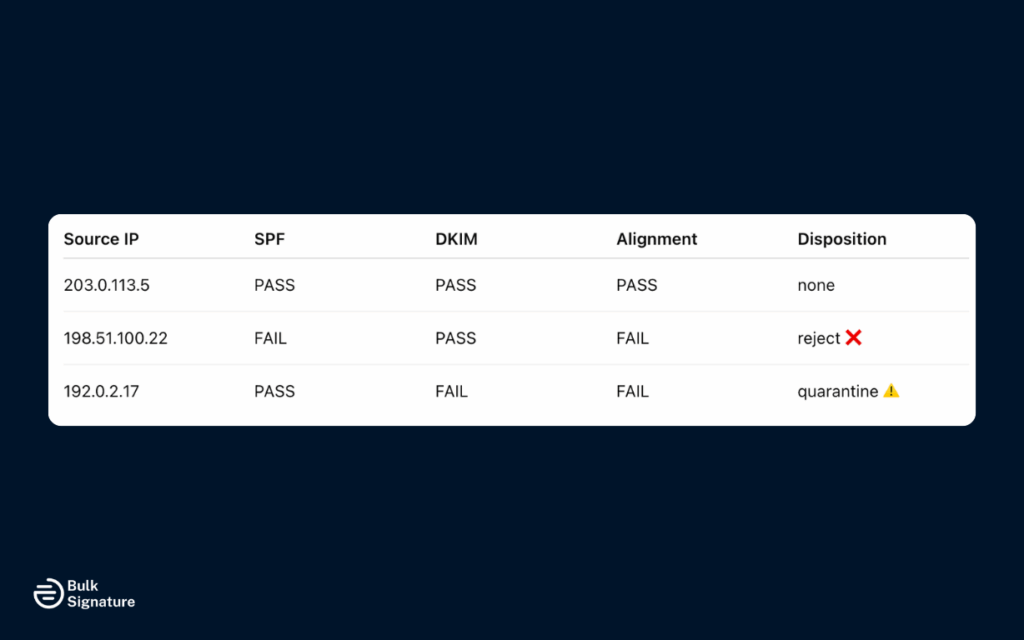
- DMARC aggregate reports summarize which sources are sending on your behalf and whether those messages passed SPF and DKIM authentication.
- DMARC failure reports provide details on individual messages that failed DMARC, including IP addresses, failed checks, and subject lines.
Use these to:
- Identify unauthorized sources spoofing your domain
- Diagnose misconfigurations from legitimate email systems
- Adjust policies based on verified performance data
Step 4: Adjust Your DMARC Policy Gradually
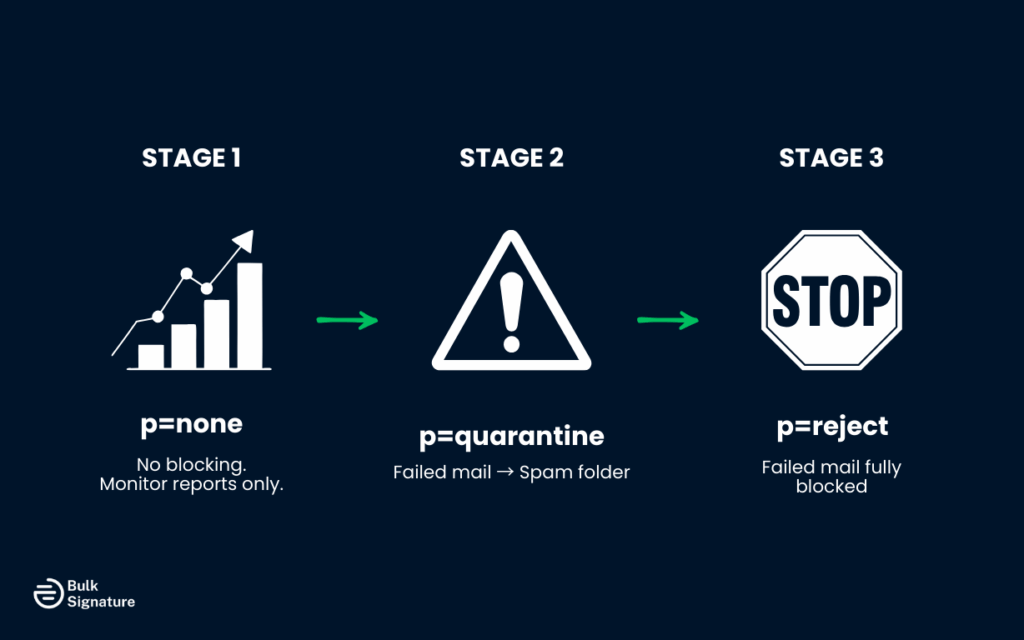
Avoid setting your DMARC policy to p=reject immediately. Instead, take a phased approach:
- p=none – No mail is blocked, but you receive DMARC aggregate reports to monitor authentication checks.
- p=quarantine – Messages that fail DMARC checks are sent to recipients’ spam folders.
- p=reject – Messages that fail SPF or DKIM alignment are fully blocked.
This staged approach ensures you can monitor and fix issues before enforcing strict policy.
Tips, Tricks, and Preventive Practices
Avoiding a DMARC fail builds a resilient email authentication system that holds up over time. These practices help you maintain strong DMARC authentication, prevent delivery issues, and improve visibility into potential phishing attacks.
Keep SPF Records Up to Date
An outdated SPF record is one of the most common reasons organizations experience DMARC failures. Every time you update your mail sending practices, like adding CRM, switching to a new email service provider, or using a marketing automation platform, you need to update the DNS TXT record accordingly.
It’s important to keep your SPF check under the 10 DNS lookup limit. You can do this by consolidating IP addresses and using include statements strategically. Regular SPF audits help eliminate outdated entries and reveal unauthorized sources trying to spoof your email domain.
Strengthen DKIM Authentication
Use 2048-bit keys for stronger DKIM signatures that provide better security while maintaining compatibility with most email service providers. Stronger keys reduce the risk of signature forgery and improve overall authentication reliability.
Apply DKIM authentication to all outgoing emails, including automated messages, newsletters, and transactional emails. Comprehensive DKIM coverage reduces authentication gaps that can trigger DMARC failures.
Rotate DKIM keys periodically to maintain security while updating DNS records to ensure continuity of authentication during key transitions. Plan key rotations carefully to avoid disrupting email delivery.
Monitor Aggregate Reports Regularly
DMARC aggregate reports and failure reports show which messages pass or fail DMARC authentication. Regular monitoring helps catch issues before they impact email deliverability.
- Set up a dedicated inbox for DMARC reports.
- Review DMARC aggregate data weekly to track SPF and DKIM authentication trends.
- Flag unexpected IP addresses or unknown sources spoofing your email domain.
- Investigate legitimate messages that fail due to SPF and DKIM misalignment.
- Identify misconfigured email service providers or outdated DNS records.
- Watch for subject lines, bounce messages, or error messages linked to failed checks.
Consistent review helps you fine-tune your DMARC policy, improve authentication, and prevent delivery failures caused by broken authentication checks.
Plan for Email Forwarding Issues
Email forwarding complicates authentication. When a message passes through an intermediate server, it may get modified, breaking the SPF and DKIM alignment that DMARC depends on. This is especially common with mailing lists or corporate email forwarding setups.
To reduce the impact, implement ARC (Authenticated Received Chain) where supported. ARC helps preserve authentication results so DMARC authentication checks at the final destination still recognize the original message as valid.
It’s also wise to test how different providers handle forwarded messages. For instance, Google Workspace users often experience failed DMARC authentication due to subtle header rewrites. Knowing how your stack handles these cases is key to maintaining compliance.
How to Read DMARC Reports
Your DMARC aggregate reports are your frontline tool for keeping bad actors out and your legitimate mail flowing reliably. Interpreting these reports helps you troubleshoot issues quickly, maintain alignment across SPF and DKIM authentication, and strengthen your domain’s reputation.
Here’s what to focus on:
- Source IP addresses: Identify where messages originate. Look for unknown or unauthorized IPs that may signal spoofing.
- SPF and DKIM results: Check if your SPF record and DKIM signature passed for each message and whether they aligned with the email domain.
- Authentication alignment: Confirm that either SPF or DKIM aligns with the “From” domain. Failures here often cause DMARC fail issues.
- Volume patterns: Track message volumes per source. Sudden spikes may indicate abuse or a misconfigured email service.
- Policy actions: See whether messages were delivered, quarantined, or rejected based on your domain’s current DMARC policy.
- Failure reports: Review detailed data for messages that failed. It’s useful for troubleshooting specific error messages, misaligned headers, or altered message content.
Why Fixing DMARC Failures Matters for Security and Trust
A failed DMARC check is a major security risk. A properly implemented DMARC policy protects your brand, blocks impersonation, and helps meet compliance standards across regulated industries.
Protecting Against Phishing Attacks
When DMARC authentication fails, your domain becomes an easy target for spoofing and phishing attacks. Cybercriminals rely on weak email authentication to impersonate trusted senders and trick recipients into clicking malicious links or sharing sensitive data.
Strong SPF, DKIM, and DMARC alignment changes that. According to Dark Reading, after Gmail enforced stricter policies in 2024, users received 265 billion fewer unauthenticated emails. That’s a 65% drop in spoofed mail.
That’s the tangible impact of proper email authentication at scale.
Safeguarding Brand Reputation
If someone uses your domain to send spoofed messages, your customers won’t know the difference—and that damages trust. Even a single phishing attack using your email domain can make recipients question whether your legitimate email is safe.
According to Validity, 84% of domains used in “From” addresses have no DMARC record at all, and fewer than 10% have one that’s valid. That leaves a massive gap for attackers, and a clear opportunity for your organization to stand out by getting it right.
Compliance and Policy Enforcement
Now, a proper DMARC configuration is expected in many industries. Sectors like healthcare, finance, and government increasingly require organizations to enforce DMARC policies as part of basic cybersecurity hygiene.
In fact, the CISA directive BOD 18-01 requires all U.S. federal civilian agencies to publish p=reject DMARC records for second-level domains. This made full enforcement a baseline expectation, not an aspirational goal.
Want to learn more about email compliance? Check out our resources:
- How to Build an Inclusive Email Signature That’s Compliant
- Security Standards and Compliance Certifications for Signatures
- What You Legally Need to Add to Your Email Signature (in Germany)
- Is an Email Legally Binding? Understanding the Legal Risks
Long-Term Email Deliverability Benefits
A solid DMARC setup improves how your domain performs across inboxes, now and as your systems evolve.
- More inbox hits: Authenticated mail lands where it should.
- Fewer bounces: Clean records reduce delivery failures.
- Stronger reputation: Trusted domains get better placement.
- Easy to scale: Config stays stable as you grow.
Simple, consistent authentication keeps your legitimate email moving without interruptions.
Make Email Authentication Scalable and Secure
As organizations grow, keeping SPF, DKIM, and DMARC aligned across teams, tools, and domains becomes harder. The more moving parts, the higher the risk of misconfigurations—and DMARC failures.
Centralized management helps by giving IT unified control over DNS records and authentication policies. It reduces drift, simplifies audits, and keeps your email domain secure.
Email signature user management platforms support consistent authentication by aligning signature practices with proper SPF, DKIM, and DMARC configuration. They help prevent spoofing, reduce delivery issues, and make security easier to maintain across departments.
Turn DMARC Errors Into a Security Win
A DMARC fail isn’t a one-time error. It’s a bigger security problem that can’t be overlooked. Fixing a DMARC error means strengthening your domain’s defenses, protecting your brand, and keeping critical communication on track.
By aligning SPF and DKIM, reviewing DNS records, and implementing a phased DMARC policy, you can turn frustrating bounces into rock-solid deliverability.
If your team needs a faster, easier way to manage email authentication at scale, BulkSignature can help, so your messages land safely and securely.
Frequently Asked Questions About DMARC Fail
What is a DMARC failure report and how do I read it?
A DMARC failure report shows which emails didn’t pass DMARC authentication, what failed (SPF or DKIM), and the IP addresses that sent them. These reports help flag misconfigurations and spot unauthorized sources using your email domain.
How do DMARC records work with DNS records?
Your DMARC record is a type of DNS TXT record that tells receiving servers how to handle messages that fail SPF and DKIM checks. It defines whether those emails should be delivered, sent to spam, or rejected.
What DMARC policy should I use for my domain?
Start with p=none to monitor without blocking mail. Once authentication is solid, move to p=quarantine, then to p=reject when all sources are properly configured. This staged rollout protects delivery while locking down security.
How do DKIM signatures prevent DMARC authentication failures?
DKIM signatures verify that the email came from your domain and wasn’t changed in transit. When configured correctly, they give DMARC the alignment it needs to pass even if SPF fails.
Why do my emails fail DMARC checks but pass SPF and DKIM individually?
DMARC requires alignment between the “From” domain and either the SPF-authenticated domain or the DKIM signing domain. If both pass but neither matches the “From” address, the message still fails. This often happens with forwarding, subdomains, or external senders.


