Phishing scams are a constant menace in email communication, with devastating consequences.
A staggering 82% of data breaches in 2023 stemmed from phishing emails, according to the Verizon 2023 Data Breach Investigations Report. Furthermore, IBM Security’s X-Force Threat Intelligence Index® 2024 highlights a rise in sophisticated phishing attempts, particularly business email compromise (BEC) scams, causing substantial financial losses.
This article equips you to fortify your defenses against these email-borne threats. We’ll delve into identifying phishing attempts, explore preventative strategies, and emphasize the importance of email security awareness.
Contents
Understanding Phishing Attacks
Phishing attacks come in various forms, all designed to manipulate recipients into compromising their security. Here’s a breakdown of some common types:
Email Phishing: This is the most widespread type, where scammers send emails disguised as legitimate sources (e.g., banks, social media platforms, delivery companies). These emails often create a sense of urgency or exploit curiosity, urging recipients to click on malicious links or download infected attachments.
Spear Phishing: This is a more targeted approach where attackers personalize emails with information specific to the recipient, like their name, company, or job title. This personalization makes the email appear more trustworthy and increases the chance of success.
Whaling: This targets high-profile individuals within an organization, such as CEOs or CFOs. The emails are meticulously crafted to appear genuine and often involve large sums of money or urgent requests, pressuring the victim into taking immediate action.
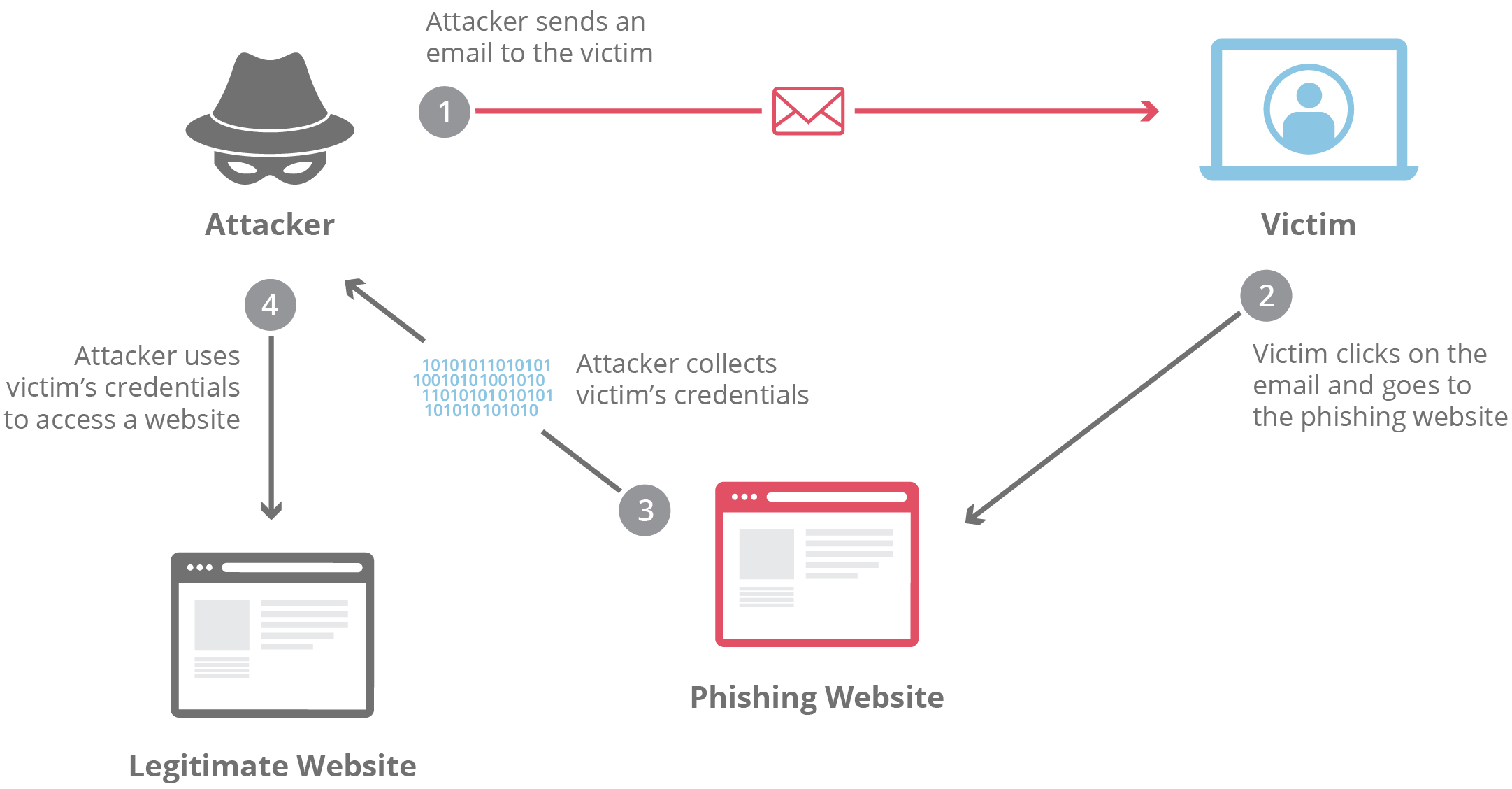
Phishing attacks rely on social engineering tactics, which are psychological manipulations that exploit human trust and emotions. Common tactics include:
Creating a sense of urgency: Emails might pressure recipients to act quickly by claiming there’s a limited-time offer, an overdue payment, or a potential account suspension.
Evoking fear: Scammers might threaten account closure, legal action, or reputational damage if the recipient doesn’t comply with their demands.
Appealing to curiosity or greed: Phishing emails sometimes offer enticing deals or exclusive information to lure recipients into clicking on malicious links.
These tactics are often combined with spoofed sender addresses that appear legitimate (e.g., mimicking a bank’s email address) and malicious attachments or links that can steal personal data, infect devices with malware, or redirect users to fake login pages.
Often fooling consumers into clicking dangerous links or giving private information, phishing assaults are even more advanced. If you use data backup software to protect your critical files and papers, you can recover your data should an attack prove successful and wipe your records. This guarantees that you have a dependable method to rapidly retrieve essential data, even in cases of system compromise.
Scheduling frequent backups made possible by data backup software helps lower data loss risk and maintain your recovery choices. Your whole cybersecurity posture can be much improved by combining firm backup plans with phishing avoidance techniques.
The consequences of falling victim to a phishing attack can be severe. Here are some potential risks:
Data Breaches: Phishing emails can trick users into revealing sensitive information like login credentials, credit card details, or Social Security numbers. This stolen data can be used for identity theft, financial fraud, or further cyberattacks.
Financial Loss: Clicking on malicious links can download malware that steals financial information or redirects users to fake payment pages, leading to financial losses.
Identity Theft: Stolen personal information can be used to open new accounts, make fraudulent purchases, or damage someone’s credit score.
Reputational Damage: Businesses that fall victim to phishing attacks can experience reputational damage if sensitive customer data is compromised.
Compromised Systems: Malware from phishing attacks can infect devices and networks, allowing attackers to gain access to sensitive information or disrupt operations.
These risks highlight the importance of being vigilant and taking proactive measures to safeguard yourself against phishing attacks.
Identifying Phishing Emails
Developing a critical eye for spotting suspicious emails is crucial for preventing phishing attacks. Here are some red flags to watch out for:
Urgency and Threats: Emails that create a sense of urgency or threaten negative consequences if you don’t act immediately are often phishing attempts.
Sender Inconsistencies: Check the sender’s email address carefully for typos, misspellings, or unusual domain names (e.g., “.ru” instead of “.com”). Hovering over the sender’s name can sometimes reveal the actual email address behind it. If you want to be consistent in your communications and avoid being categorized as spam, start using email signature software now.
Unprofessional Formatting: Poor grammar, typos, or a lack of personalization can indicate a phishing email. Legitimate companies typically maintain a professional tone in their communications. If you are in communications, you can avoid such pitfalls with email marketing tools.
Suspicious Attachments and Links: Be wary of unsolicited attachments or links, especially those with generic names or extensions you’re unfamiliar with. Never click on a link or download an attachment from an unknown sender.
Unrealistic Offers: Emails promising too-good-to-be-true deals or exclusive information are likely scams.
Here are some additional tips for identifying phishing emails:
Verify the Source: If you’re unsure about the legitimacy of an email, contact the sender directly using a verified phone number or website (not the information provided in the email).
Be Cautious of Unexpected Requests: Businesses wouldn’t typically request sensitive information via email. If you receive an unexpected request for personal details, contact the company directly to confirm its authenticity.
By familiarizing yourself with these red flags and practicing caution with suspicious emails, you can significantly reduce the risk of falling victim to a phishing attack.
Strategies to Prevent Phishing Attacks
A layered approach to email security is essential for effectively preventing phishing attacks. This strategy combines three key elements:
User Awareness and Training
Employee Training
Organizations should prioritize regular training sessions to educate employees on phishing tactics and the red flags that can help them identify suspicious emails. Training can equip employees with the knowledge to:
Recognize common social engineering tactics used in phishing attempts.
Identify red flags in emails, such as urgency, sender inconsistencies, unprofessional formatting, and suspicious attachments/links.
Practice caution when dealing with unexpected requests for personal information via email.
Report suspicious emails to the IT department for further investigation.
Technical Safeguards
Strong Spam Filters: Implementing robust spam filters can significantly reduce the number of phishing emails reaching inboxes. Regularly updating spam filters ensures they can detect and block new phishing tactics.
Email Authentication Protocols: Protocols like DKIM and SPF help verify the legitimate sender of an email by ensuring the email domain matches the sender’s address. This helps prevent spoofing, a common technique used in phishing attacks.
Integration with Security Solutions: Some email security solutions can integrate with tools like Bulksignature.com (without explicitly mentioning the product here). This integration can potentially enhance email security by allowing for features like:
Automatic detection of phishing attempts based on advanced threat intelligence.
Banner warnings within emails to alert users about potential phishing risks.
Secure link rewriting to prevent users from clicking on malicious links accidentally.
Secure Email Practices
Strong Passwords: Encourage users to create strong and unique passwords for their email accounts and enable multi-factor authentication (MFA) for an additional layer of security.
Scrutinize Attachments and Links: Advise users to avoid opening attachments or clicking on links from unknown senders. Always verify the legitimacy of a link by hovering over it before clicking and ensuring it leads to the intended website.
Avoid Sharing Sensitive Information: Emails are not a secure way to transmit sensitive information like passwords or credit card details.
Report Phishing Attempts: Encourage users to report suspicious emails to the IT department so they can be investigated and blocked from reaching other users.
By implementing these strategies, organizations and individuals can significantly reduce the risk of falling victim to phishing attacks and create a more secure email environment.
DKIM/DMARC/SPF as an Ultimate Solution for Preventing Phishing Attacks
DKIM, SPF, and DMARC are a powerful trio for email authentication and significantly improve your organization’s defense against phishing attempts. Here’s a breakdown of the setup process
SPF (Sender Policy Framework): Acts like a whitelist, specifying authorized IP addresses to send emails for your domain.
DKIM (DomainKeys Identified Mail): Digitally signs emails with a cryptographic key, verifying their origin and preventing tampering.
DMARC (Domain-based Message Authentication, Reporting & Conformance): Oversees the process, tells receiving servers how to handle unauthenticated emails (reject, quarantine, etc.), and provides reports for analysis.
How to setup DKIM, SPF, and DMARC
As a system administrator, you can significantly reduce the risk of phishing attacks by implementing DKIM, SPF, and DMARC. Here’s a detailed set of steps you need to do for the proper setup:
1. Setting Up SPF (Sender Policy Framework):
Find your DNS Management Console: This is a web interface provided by your domain registrar or hosting service where you can manage your domain’s DNS records. It’s usually found within your account dashboard.
Create a TXT Record: A TXT record stores text information associated with your domain. Click on Add Record or a similar option in your DNS management console. Choose TXT as the record type.
Craft your SPF Policy: This policy specifies authorized email servers for your domain. It’s a text string with specific syntax. There are many online tools and wizards offered by domain registrars to help you build your SPF record. These tools typically ask you to enter the IP addresses or hostnames of your email servers.
Publish the SPF Record: Copy the generated SPF policy text string and paste it into the “Value” or “Data” field of the TXT record you created. Save the record. Propagation may take up to 48 hours for the changes to take effect globally.
2. Enabling DKIM (DomainKeys Identified Mail):
Check your Email Service Provider (ESP): Most ESPs (like Gmail Workspace or Microsoft 365) offer DKIM signing by default. Look for DKIM settings in your ESP’s admin console. If DKIM isn’t enabled, consult your ESP’s documentation for specific instructions.
Generate a DKIM Key Pair: The ESP will generate a cryptographic key pair consisting of a public key and a private key. The private key is like a secret password and needs to be kept secure on your email server. The public key will be used for verification.
Publish the DKIM Public Key: The ESP will provide you with the public key in a specific format (often starting with “v=DKIM1”). You’ll need to create another TXT record in your DNS management console similar to the SPF record creation process. Paste the public key text string into the “Value” or “Data” field and save the record.
3. Configuring DMARC (Domain-based Message Authentication, Reporting & Conformance):
Craft a DMARC Policy: DMARC tells receiving servers how to handle emails that fail SPF or DKIM authentication. There are three policy options (p=):
p=none (Reporting Only): This is a good starting point. Receiving servers will perform SPF and DKIM checks but won’t take any action on failures. You’ll receive reports on authentication results.
p=quarantine: Emails failing authentication are quarantined for review.
p=reject: Emails failing authentication are rejected outright.
Create a DMARC Record: Similar to SPF and DKIM, create a TXT record in your DNS management console. Use a specific format for the DMARC policy, including the chosen policy (p=), and the email address where you want to receive DMARC reports ( rua:). Many online tools can help you generate the DMARC record.
Set Up a Reporting Mailbox: Create a dedicated mailbox for receiving DMARC reports. This mailbox address should be the one specified in the DMARC record (rua:). DMARC reports provide valuable insights into email authentication attempts for your domain.
Things to Keep in Mind
Phased Implementation: Start with a reporting-only DMARC policy (p=none) for a period to identify any issues with email deliverability before enforcing stricter policies.
Double-Check Record Syntax: Ensure proper syntax for your SPF, DKIM, and DMARC records to avoid authentication failures. Many online tools can validate your records before publishing them.
DKIM Signing Server Authorization: Verify that the servers your ESP uses for DKIM signing are authorized to send emails from your domain in your SPF record. This prevents SPF failures.
By following these steps and consulting your ESP’s documentation for specific details, you can implement DKIM, SPF, and DMARC to significantly improve your organization’s email security posture and make it much harder for phishers to impersonate your domain.
Building a Culture of Email Security
Phishing attacks remain a persistent threat in today’s digital landscape. However, by adopting a layered approach to email security, individuals and businesses can significantly strengthen their defenses. This approach combines user awareness training, robust technical safeguards, and secure email practices.
Equipping employees with the knowledge to identify phishing attempts is crucial. Regular training sessions can empower them to recognize red flags and act cautiously when encountering suspicious emails. Implementing technical safeguards like strong spam filters and email authentication protocols can further bolster email security by filtering out malicious emails and preventing sender spoofing. Finally, encouraging secure email practices, such as using strong passwords and avoiding sharing sensitive information via email, further minimizes the risk of falling victim to these scams.
Building a culture of email security awareness is an ongoing process. By prioritizing user education, implementing robust security measures, and fostering a culture of vigilance, organizations and individuals can create a more secure email environment and significantly reduce the risk of falling victim to phishing attacks. You can further bolster email security with email signature software.